Lessons Learned from 2018’s Biggest Information Security Stories
by Commonwealth Financial Network
 As the media knows, fear sells. These days, it can become a challenge to separate fact from fiction when reading the headlines. For example, a USA TODAY article from earlier this year reports on children succeeding in a “hack-the-election” event, while Slate Magazine tells a different side of the story about the same event.
As the media knows, fear sells. These days, it can become a challenge to separate fact from fiction when reading the headlines. For example, a USA TODAY article from earlier this year reports on children succeeding in a “hack-the-election” event, while Slate Magazine tells a different side of the story about the same event.
With 2018 coming to a close, let’s get our facts straight on five of the most important information security stories from this year. Along the way, we’ll pick up some tips to better protect against cyberthreats.
In January, we caught wind of two major chip flaws, Meltdown and Spectre, which potentially affect all modern computing devices. (They’re reported to affect all Intel-based processors since 1995; it isn’t clear how many AMD-based processors they’ve affected.)


In a nutshell, Meltdown and Spectre allow programs on your machine to read sensitive information from other programs, which could potentially be abused by an attacker. If you’d like to read more on these vulnerabilities, www.meltdownattack.com breaks it all down without getting too technical.
What to do: The risk of an attacker successfully exploiting Meltdown or Spectre can be greatly reduced with security patches, which come with your regular updates. So be sure to complete all software updates as soon as you’re prompted. In addition to Windows, macOS, Java, and Adobe programs, you’ll want to consider your firewall, additional software you’ve installed, and your mobile devices. (At Commonwealth, as part of our Shield program, we take care of a great deal of these updates for our advisors.)
In May, Twitter exposed passwords within its own internal systems (i.e., not out on the Internet for anyone to see). These passwords were meant to be hashed, which is how most websites store passwords securely; however, Twitter users’ passwords had accidentally been stored in an internal log before the hashing process began.
Twitter reported that there was no evidence of anyone misusing these passwords, but it’s always better to err on the side of caution. Even Twitter can’t say with absolute certainty that no one gained access to these passwords.
What to do:
- Change your Twitter password if you haven’t since May.
- If you reused your Twitter password for other online accounts, change those passwords as well.
- Be sure to enable multifactor authentication on Twitter.
While you’re at it, it’s best to add multifactor authentication to any account worth protecting. That way, even if your password is compromised, an attacker would still need that second form of authentication (like your phone) to access your account.
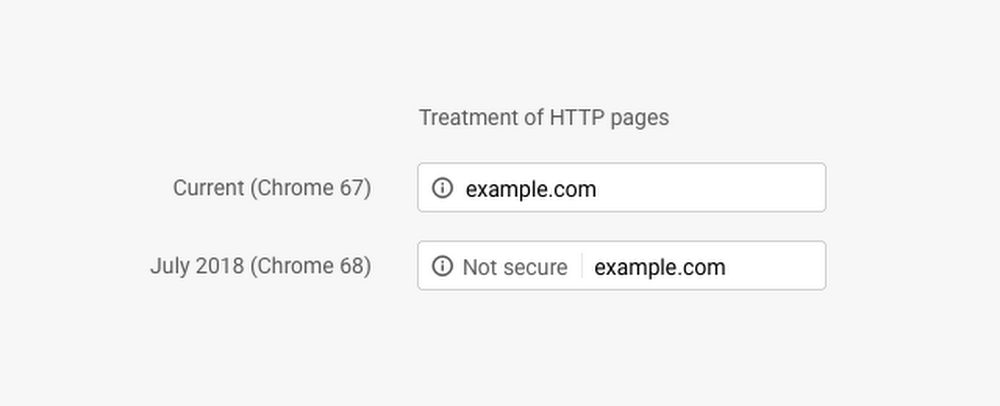
According to Medium, from 2017 to 2018, there was an 18-percent increase in the website adoption rate of HTTPS. Part of this increase is fueled by popular browsers like Google Chrome “shaming” sites that begin with HTTP. Starting with Chrome version 68, if you visit a site that begins with HTTP instead of HTTPS, you’re given a warning that it may not be secure.
Source: Google
What’s so significant about adding a letter to these URLs? With HTTPS, all the traffic between you and that website is encrypted; that way, if an attacker were to intercept that traffic, he or she wouldn’t be able to read it. This is especially critical when entering sensitive information (like password or payment information). The push to HTTPS will help make the Internet a safer place for everyone.
What to do: Keep your browser up to date, as newer versions will help flag HTTP sites. There’s no problem with casual browsing on HTTP websites, but if you’re inputting any sensitive information, be aware that it could potentially be intercepted, as HTTP does not encrypt traffic.
I’m sure you’ve read at least one of the many articles about Facebook’s privacy issues this year, from the Cambridge Analytica scandal, to reports of Facebook scanning private messages, to a bug that inadvertently turned millions of private posts public. These stories all have one common theme: Facebook doesn’t protect our information the way we expect it to.
What to do:
- Review your social media privacy settings and adjust them as necessary.
- Limit the data you provide to social media accounts.
Social media is all about sharing with others. Although it’s tempting to share everything you can, some information should be left offline, especially if its exposure could put you at risk.
After the 2017 Equifax breach, Congress passed a bill (which was signed into law) to make credit freezes free starting September 21, 2018. Previously, credit freezes cost up to $10 per bureau, and in some states, that cost applied each time someone froze or unfroze his or her credit.
Dropping the fees from this tool makes protecting our identities significantly easier. With a freeze, your credit file is frozen in place so that no one can open a new line of credit in your name. And if you do have a new loan or credit card on the horizon, you can temporarily lift the freeze for a specific company or time frame
What to do: Putting a credit freeze in place is one of the most effective ways to protect yourself against identity thieves. You can start by going to the official websites of the three credit bureaus: Equifax, Transunion, and Experian. You’ll need to remember to lift the freeze whenever you want to open a new line of credit or get a hard credit inquiry, but otherwise, there isn’t much maintenance involved.
Despite how unexpected some of these stories are, none of these recommended actions take much work to incorporate into your own day-to-day habits. Here’s a quick-hit list of the most important lessons from these five information security stories to help you protect against cyberthreats:
- The longer you delay an update, the longer you may be vulnerable to the latest malware. Always keep software up to date.
- When working with sensitive information, opt for HTTPS over HTTP.
- Breaches and other security incidents are beyond our control. The most we can do is minimize the impact by:
- Using different passwords for different accounts
- Enabling multifactor authentication
- Understanding and adjusting any privacy or security settings
- If you’re uncomfortable with the data your social media profile collects, limit the data you share.
- Consider a credit freeze, as it’s one of the best tools for protecting against identity theft.
What best practices does your firm follow to protect against cyberthreats? Have you made any changes to your cybersecurity practices in light of recent information security stories? Please share your thoughts with us below!
Commonwealth Financial Network is the nation’s largest privately held independent broker/dealer-RIA. This post originally appeared on Commonwealth Independent Advisor, the firm’s corporate blog.
Copyright © Commonwealth Financial Network















